|
|
Protection for Voice-over-IP (VoIP) Phone Calls
The threat of listening in on VoIP phone calls via ARP attacks. A new network security threats consists in attacking Voice-over-IP telephone calls (VoIP phone calls) via ARP spoofing attacks. Like any other network protocols, all VoIP phone calls can be tapped by ARP man-in-the-middle-attacks. The easiest way for an attacker to listen in on phone calls consists in ARP attacks. Tools for this type of malicious activity are available on the Internet, for instance with the Cain and Abel tool. The attacker is well sheltered from prosecution, as still only a few enterprises and organisations have reliable monitoring tools available, which securely protect them against the severe ARP spoofing threat. Any person can shadow VoIP phone calls, if at least one caller is sitting close to the attacker. Executives are worried that their staff or intruders tap their telephone and monitor their phone calls. Is your company utilising VoIP? Or are you planning to implement VoIP phone connections within your company? If so, it will be indispensible for you to make any attempts impossible to tap the company's telephone lines via ARP spoofing.
Press
and media about us on the topic of ARP-Spoofing and VoIP
ARP Guard ready to install. Should you wish to obtain an offer on how to protect the voice-over-IP network resources of your company or your organisation, please contact us or use this form to obtain a quote for having ARP Guard installed at your premises.
Interesting articles on Voice-over-IP and ARP spoofing Here your find a selection of interesting
articles on the topic of tapping
VoIP phone calls, attacking
VoIP, ARP spoofing attacks on VoIP, etc.
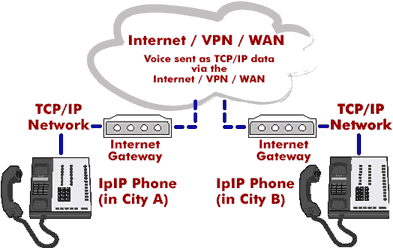
Typical Voice-over-IP (VoIP) phone calls - overview:
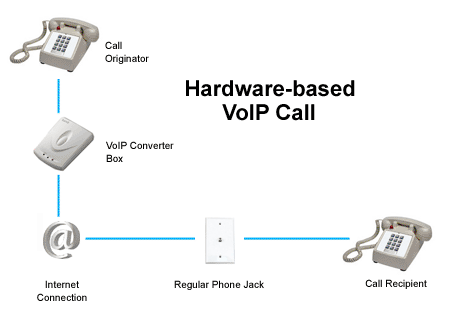
Voice-over-IP (VoIP) phone calls with regular phones - overview:
Companies with a focus on voice-over-IP (VoIP) can become a merchant for this valuable IT security product.
Thank you very much for your interest in our network security division and our ARP spoofing protection products.
ARP attack software can be downloaded
for instance from
|
* Home * Network Security * E-Business Products * Investment *
* Jobs * Links * Sustainable Development *
* Contact *