|
|
ARP Guard - Protection from ARP Spoofing Attacks
The threat of ARP attacks. External attacks by hackers, viruses, worms and trojans are permanent threats to any progressive company. What is not widely known, though, is that the major portion of attacks come from within the network. In 2002 KPMG reported that up to 80 % of all intrusions were initiated internally, from inside a company network. Technical ignorance, curiosity and intentional manipulation of data often lead to serious damages for organisations.
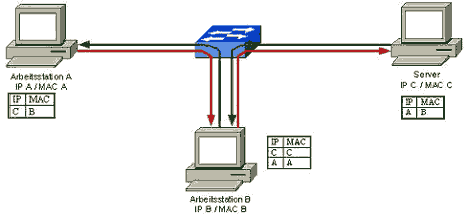
Internal network attacks are typically operated via so called ARP Spoofing or ARP Poisoning attacks. Malicious software to run ARP Spoofing attacks can be downloaded on the Internet by everyone. Using fake ARP messages an attacker can divert all communication between two machines with the result that all traffic is exchanged via his PC. By means of such a man-in-the-middle attack the attacker can in particular
These ARP attacks are usually successful even with encrypted connections like SSL, SSH or PPTP. ARP belongs to the OSI data link layer (layer 2).
The symptoms of ARP spoofing attacks are:
ARP spoofing attacks protection. ARP Guard is a system that forms an active protection shield against internal ARP attacks. The ARP Guard early warning system constantly analyzes all ARP messages, sends out appropriate alerts in real-time and identifies the source of the attack. This protection system from ARP spoofing attacks can be configured not only to raise an alarm, if an ARP attack has been sensed, but even to automatically defend against the attacker. ARP Guard easily integrates with your existing IT security environments, such as firewalls, virus scanners, or intrusion detection systems, and forms an active and reliable shield against ARP spoofing.
More information
Media and press about us Press and media about us on the topic of ARP-Spoofing and VoIP >>
ARP Guard ready to install. Should you wish to obtain an offer on how to protect the network resources of your company or your organisation against ARP spoofing, please contact us or use this form to obtain a quote for having ARP Guard installed at your premises.
For more general information about ARP, please click here >>
* * * * * *
Interesting articles on ARP spoofing and ARP poisoningAngriff
von Innen The
Insider Threat Study Angriff
von Innen
Become a merchant for this IT security product IT companies with a network and security focus can become a merchant for this valuable IT security product.
Our Distribution and ARP Guard Installation Partners
ARP attack software can be downloaded
for instance from
Thank you very much for your interest in our network security division and in our ARP spoofing protection products.
|
* Home * Network Security * E-Business Products * Investment *
* Jobs * Links * Sustainable Development *
* Contact *